For Colasoft Capsa you can get an easy use but advanced network traffic monitoring, protocol analysis and diagnosis view software. It is a specialist to help you solve LAN troubles. ARP, because of its simpleness, fastness, and effectiveness, is becoming increasingly popular among internet raggers, thus causing severe influence to the internet environment.With Colasoft Capsa, we can quickly and accurately locate ARP source when ARP attack happens to the network, so as to ensure normal and reliable network operation.
We have four basic solutions to locate ARP attack with Colasoft Capsa:
View ARP diagnosis events in the Diagnosis View;
View ARP request and response packets in the Protocol View;
View original information of ARP packets in the Packets View;
View node information in the Endpoints View;
Solution one:
Diagnosis View is the most direct and effective place to locate ARP attack and should be our first choice. Its interface is displayed as picture1.
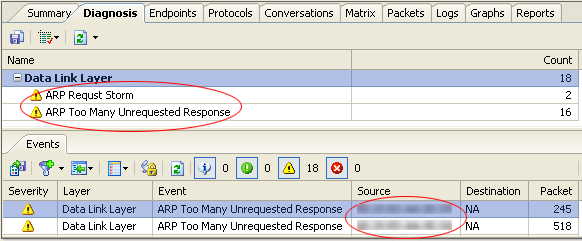
Picture 1 definitely points out that there are two kinds of ARP attack event, ARP Too Many Unrequested Response and ARP Request Storm, in the network, and the attack source is clearly given at the bottom. Meanwhile, Capsa will provide reasons of such ARP attacks and corresponding solutions.
Solution two:
The status of ARP packets are displayed in the Protocol View, like in picture 2. Here we must pay special attention to the value of ARP Request and ARP Response. The ratio of ARP Request and ARP Request should be approximately 1:1 under general condition. If there is a great difference between these two values, there may be ARP attacks in the network.
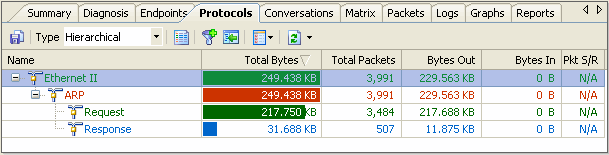
In picture 2 there are 3484 ARP Request packets but only 507 ARP Response packets, by comparing these two values, we can presume there are ARP attacks in the network.
Solution three:
Packet decoding information in the Packets View can tell us the original information of ARP packets, please look at picture 3.
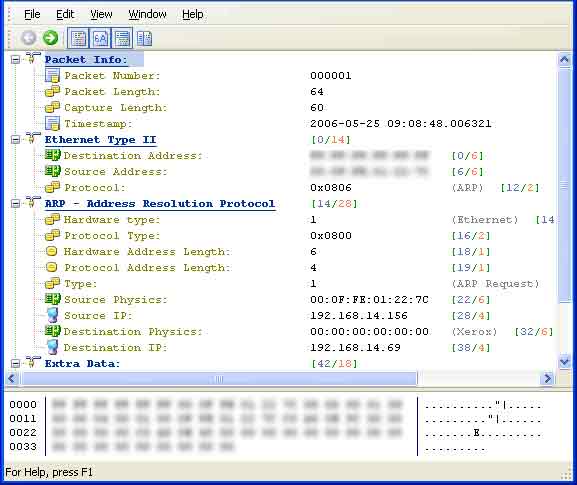
(Picture 3)
By decoding ARP packets, we can find out the source and destination of the ARP packets, the function and the reality of these ARP packets.
Solution four:
Identify ARP attack in the Endpoints View. (See picture 4)
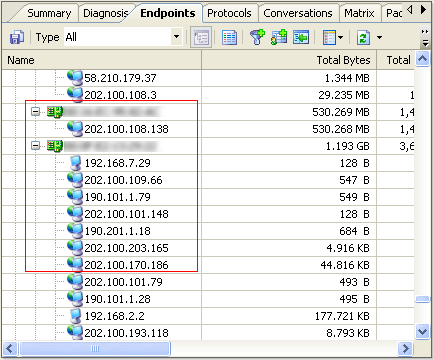
(Picture 4)
In the Endpoints View we can view the correlation of MAC address and IP address. Generally speaking, one MAC address shall have only one IP address corresponding to it. If one MAC address has multiple IP addresses to it, the condition may be:
- the host with the MAC address is the gateway;
- these IP addresses are bound to the MAC address manually;
- ARP attack
So, the Endpoints View can also give us a hint to locate ARP attack.
In addition, the Matrix View allows us to see communication information between those hosts in the network, which helps us to fast identify abnormal conditions and locate the attack source.
(Matrix View)
Conclusion
ARP, as one of the most popular attacks in recent days, may cause severe problems to our network. How to fast troubleshoot ARP attacks is what every network administer concerns. Colasoft Capsa will greatly enhance network administrators’ capability to identify ARP attacks and protect the network from ARP attacks, so as to ensure normal network operation. Besides fast locating ARP attacks, Colasoft Capsa can also analyze network abnormities, locate failure nodes, enhance network security, evaluate and improve network performance.
No comments:
Post a Comment